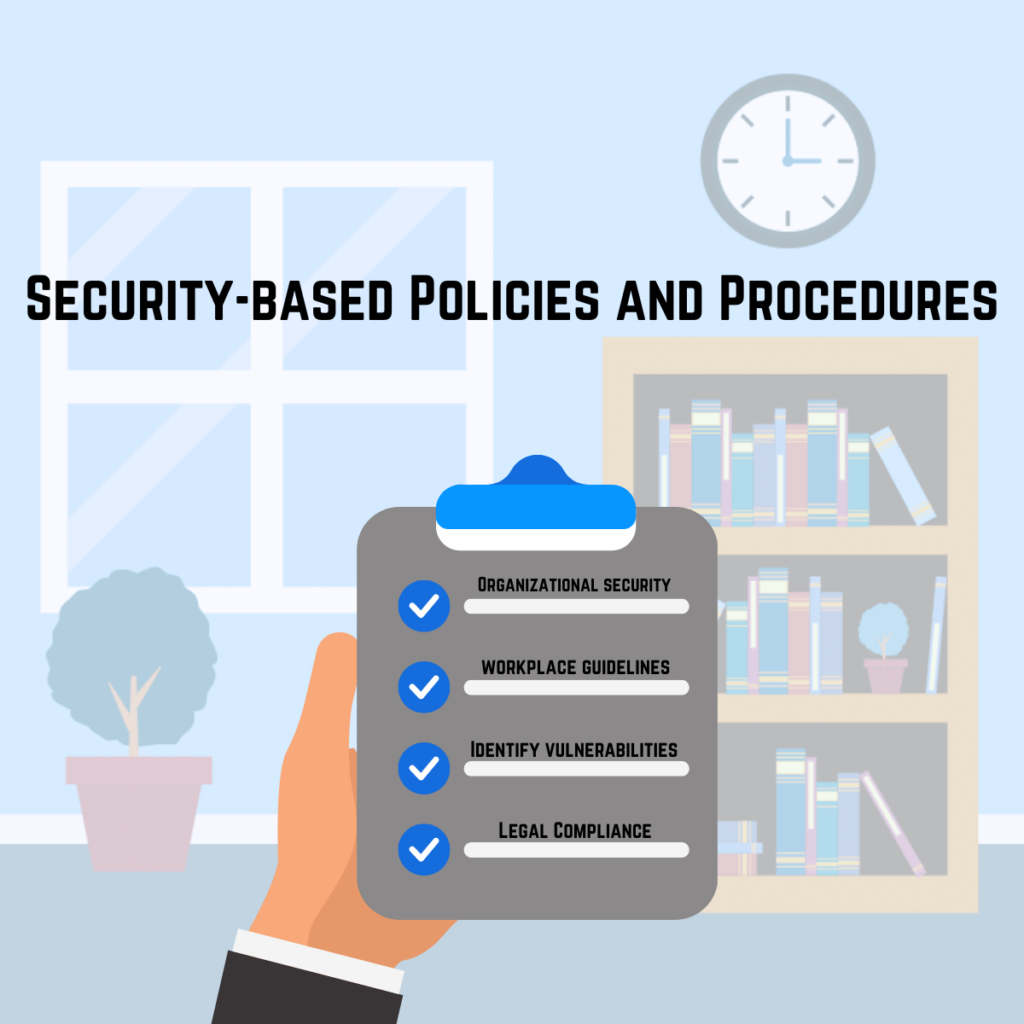
Security-based policies and procedures are essential in protecting organizations’ sensitive information from cyber threats. These policies and procedures outline guidelines and best practices that employees must follow to safeguard information and assets from unauthorized access, theft, or compromise. In today’s world, where cyber-attacks have become increasingly sophisticated and frequent, organizations must prioritize implementing these policies and procedures to mitigate risks and prevent potentially catastrophic breaches.
One of the main benefits of security-based policies and procedures is that they provide a framework for employees to follow to ensure that they comply with security measures. This includes guidelines for password strength, data encryption, access controls, and other security measures. When employees follow these policies, they help to create a secure culture within the organization that reinforces the importance of security.
Security-based policies and procedures also help to protect the organization from potential legal liability. By implementing security measures that comply with industry standards and regulations, organizations can demonstrate that they have taken reasonable steps to protect sensitive data. This can be crucial in a data breach or other security incident, as it can help reduce the severity of legal and financial repercussions.
Another benefit of security-based policies and procedures is that they promote consistency and efficiency in security practices. Managing security risks and vulnerabilities becomes easier when all employees follow the same guidelines. This also makes tracking and auditing security measures easier, which can help demonstrate compliance and identify areas needing improvement.
Security-based policies and procedures are critical in today’s cyber threat landscape. They provide a framework for employees to follow, protect the organization from legal liability, and promote consistency and efficiency in security practices. Organizations can create a security culture by prioritizing implementing these policies and procedures and reducing the risk of potentially catastrophic breaches.
If your organization does not have someone already focused on writing and consistently reviewing your security-based policies and procedures, Masser Technologies can server as your virtual chief information security officer, or vCISO. Contact us today to learn how!